SQL injection (SQLi) attacks may destroy your database. These attacks are one of the most common attacks on websites (it is in the OWASP Top Ten). This attack relies on injecting code into SQL database queries through the user input.
WARNING: We’re not responsible for damage caused by SQL injection! Malicious hacking is a computer crime and you may face legal consequences! This post is meant to gain awareness about SQL injection and give a way to prevent those vulnerabilities.
The impact of SQL injection
SQL injection attacks may result in unauthorized access to sensitive data, such as:
- Passwords
- Credit card information
- Personal user information
- Information normally hidden from website users
SQL injection attacks have been used in many data breaches over the years, which then caused damage to the reputation and regulatory fines.
SQL injection types
SQL injection can be divided to:
- Error-based SQL injection - injection is done with help of error messages.
- Union-based SQL injection - injection is done with help of
UNIONclause. - Blind SQL injection - it is possible to extract the data with help of generated content
- Time-based SQL injection - injection is done with help of response delays
Example: vulnerable web application
Sorry, we didn’t do it in server-side JavaScript this time…
This is an example of PHP web application vulnerable to SQL injection:
1 | <!DOCTYPE html> |
If you want to try it, there is a database structure in SQL, along with mock data (the database name is studentdb, DBMS is MySQL/MariaDB):
1 | -- phpMyAdmin SQL Dump |
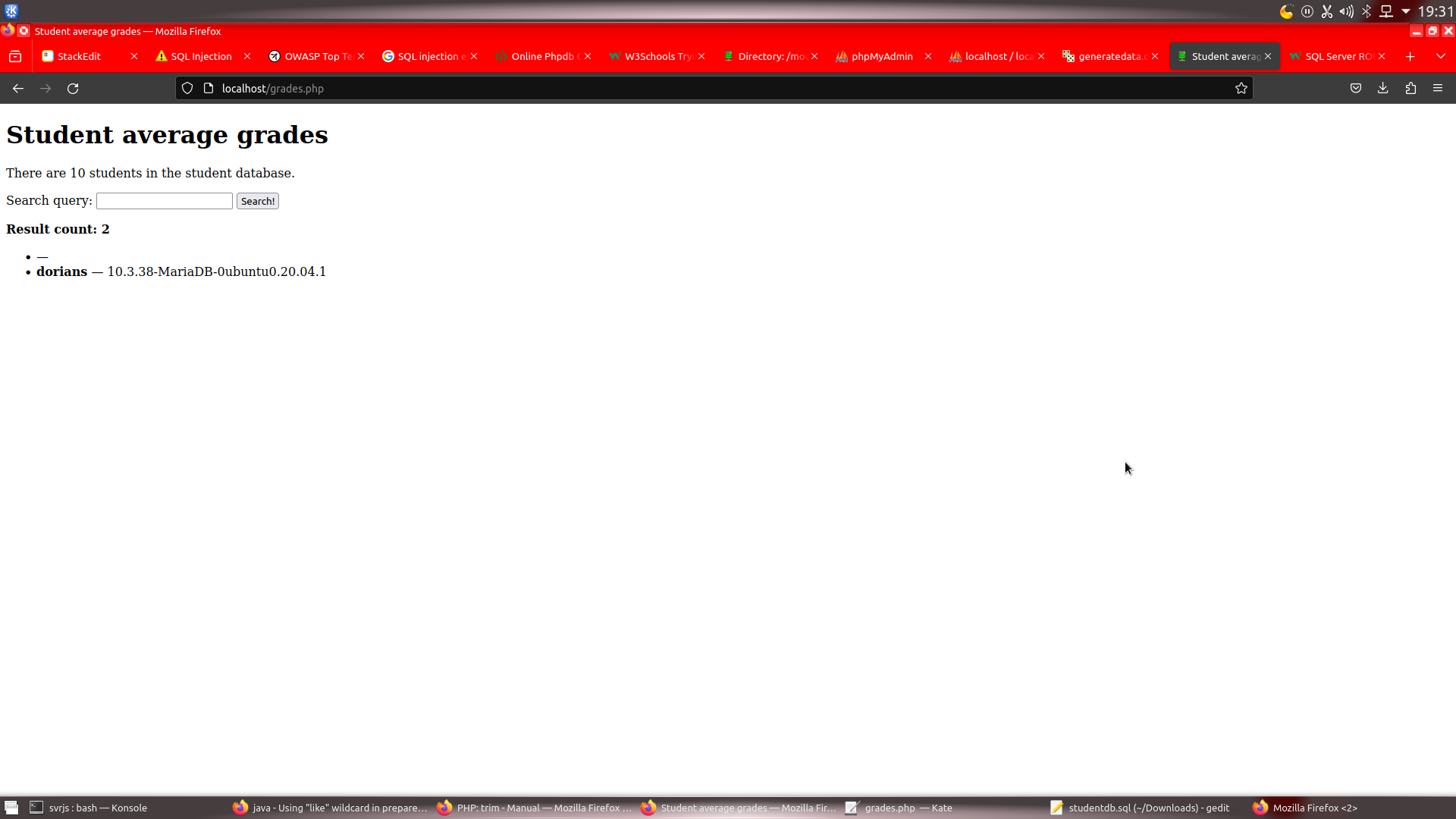
If you type something (for example “John Smith”), then the SQL query will look like this:
1 | SELECT students.name AS name, ROUND(AVG(grades.grade), 2) AS average FROM grades INNER JOIN students ON students.id = grades.studentid WHERE students.name LIKE '%John Smith%' GROUP BY grades.studentid; |
And the web application will look up student names containing the substring “John Smith”. With this example set of data, web application would return 0 results, because there are no matching entries.
The problem is the lack of database input sanitation. What happens, if the input was ' OR 1=1#?
The SQL query will then look like this:
1 | SELECT students.name AS name, ROUND(AVG(grades.grade), 2) AS average FROM grades INNER JOIN students ON students.id = grades.studentid WHERE students.name LIKE '%' OR 1=1#%' GROUP BY grades.studentid; |
There will be then OR 1=1 in the query, which is always true, thus returning all the students’ average grades. The result page will display only one result due to removal of GROUP BY clause. The “#” character makes rest of the query a comment.
Does the SQL query above look a bit dangerous? What if the input was asd' UNION SELECT @@hostname, @@version #?
The SQL query will then look like this:
1 | SELECT students.name AS name, ROUND(AVG(grades.grade), 2) AS average FROM grades INNER JOIN students ON students.id = grades.studentid WHERE students.name LIKE '%asd' UNION SELECT @@hostname, @@version #%' GROUP BY grades.studentid; |
Then the server hostname and DBMS version will be leaked.
Some websites even allow batched SQL statements like with asd'; DROP TABLE students# input. The SQL query will then look like this:
1 | SELECT students.name AS name, ROUND(AVG(grades.grade), 2) AS average FROM grades INNER JOIN students ON students.id = grades.studentid WHERE students.name LIKE '%asd'; DROP TABLE students#%' GROUP BY grades.studentid; |
Then the students table will be deleted. The data will be lost.
SQL injection using batched SQL statements is summarized in this xkcd comic: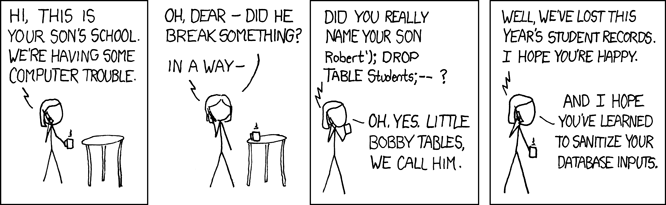
Oh no! Hackers will hack that site pretty easily! What you can do?
SQL injection prevention
Fortunately there are many ways of protection against SQL injection.
If you want to use escaping, then it depends on programming language you use. In PHP and mysqli driver, you can use mysqli_real_escape_string($conn, $input) function. In server-side JavaScript and mysql library, you can use mysql.escape(input) function (where mysql is a instance of mysql module).
There is an example of fixed web application (using mysqli_real_escape_string function):
1 | <!DOCTYPE html> |
In this example, mysqli_real_escape_string function escapes various characters causing database problems. Escaped characters will then be treated as regular characters instead of string terminators, thus mitigating SQL injection vulnerability.
But there is one problem, it doesn’t work for number inputs. In this case, you can validate the input using a regular expression, like this:
1 | if(preg_match("/^[0-9]+$/", $input)) { |
This code checks using a regular expression if the input is a number. If it’s not a number, then it rejects the input with an Invalid input! error message.
You can also use prepared statements. Prepared statements separates SQL from data, effectively mitigating SQL injection vulnerability. Example code:
1 | <!DOCTYPE html> |
In this example, SQL query and search query data are kept separated, thus mitigating SQL injection.
With these mitigations, your website will be harder for hackers to break.
UPDATE: PHP code edited to not exhaust MySQL/MariaDB database connection limit.